Hello Everyone, Welcome to Fixingblog.com
Do You Want To Secure Your Belkin router? As We Have Been Expert Fixing Most Of Router Problems –
Today In This Post We Will Explain To You How To Lock And Password Protect Your Belkin Wireless Network.
Important Facts Before You Setup Password To Belkin –
Dear Friends, We Would Like To Crack This Confusion Between Router Users And Clear The Concept
- Router Password And Wireless Network Password Is Totally Different Things.
- While Router Password Locks and Prevent unauthorized access To Router Settings and Configuration.
- Wireless Password Makes The Wireless Internet Secured And Allow Only Users Who Know The Password.
So Don’t Be Confused Let’s Go and Safeguard Your Belkin router.
Read More: How to setup Belkin wireless router
Password Protect Belkin Wireless
Using An Unsecured Wireless Router Can Cause Many Problems like Other People Can Use Your Internet, Internet Slow Or Sometimes Network Can Be Compromised.
Please Follow this Instruction To Secure Belkin Wireless Router-
- Login To Your Belkin Router Using Default IP Such As 192.168.2.1
- Type This IP Address On top Of Your Browser and Press Enter and Login.
- It May Asks router Password For Login Leave It Blank and Press Submit.
- Now Click On Advanced Settings at Wireless Go to Security And You May See Your Security Mode Disabled.
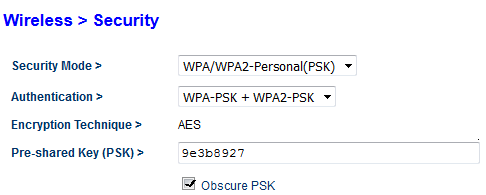

- Please Enable Your Security Mode And Select WPA/WPA2-PERSONAL(PSK).
- Now In Authentication Please Select WPA-PSK+WPA2-PSK
- In The encryption, Technique Make Sure It’s Selected To Be TKIP+AES
- Now Type The Password Where Its Says And Try Making A Complex Password.
- Please Check On Obscure PSK And Apply The Changes And It’s Done
- Reboot Your Router After 1 Min And Done.
Good Job Now Your Have Secure Belkin Wireless Router.
Give Your Password To Only People You Trust And They Can Connect To the Internet. Read More: Why Belkin wireless router is not working?
Please Don’t Forget To Update The Belkin Router For better Security. Updates Fix Many Issues In Security And Performance. Read More: How To Update Belkin Wireless Router Firmware?
Since We Have Secured The Belkin Wireless We Should Also Consider To Secure The Router Setup And Configuration.
Change Belkin Router Default Password
Dear Friends As We Have Explained Before That Router Password Is For Accessing The Router Settings And Configuration and Wireless Password Is For Accessing The Internet.
In the Above Lines, We Have Explained How To Secure The Wireless Connection Now We Will Guide You on How to Lock And Secure The Belkin Router Setup Page –
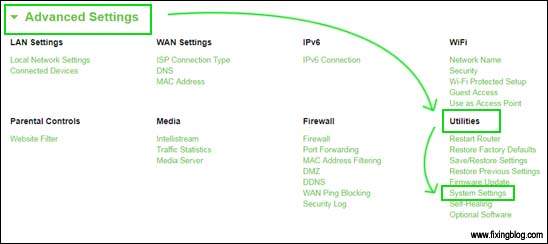
- Login To Belkin Router Using 192.168.2.1 And Click on Advanced settings then Go to Utilities
- Under Utilities Go to System Settings Here You Can See Many Options.

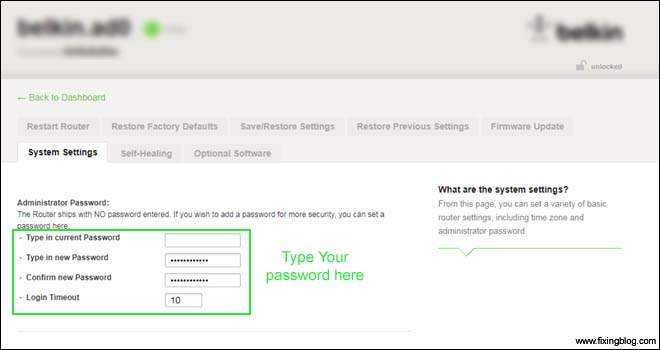
- In Old Belkin Models You can Leave the Place Blank For Old Password.
- For New Belkin Models Please Remove the Password.
- Type The New Password And Apply The Settings.
- Reboot the Router And Check the Dashboard.

If Any Of This Did Not work Please Reset the Belkin router.
We Are Confident That All This Information Will Help You Secure Belkin Wireless Router. Comment Below And Please Let Us Know If You Need Any Other Help With Belkin router Security And Settings.
Please Share This Post If You Find it Worth Spreading. We Thank You For Reading At Fixingblog.com
